Create Canary Credentials with Traitorbird
1. Create Token
After creating an account, choose "create token" to create a new canary token credential from your tokens list. A normal account costs $49/year or local equivalent – we don't offer a free trial, but contact us if you have any questions or problems and we'll sort it out.
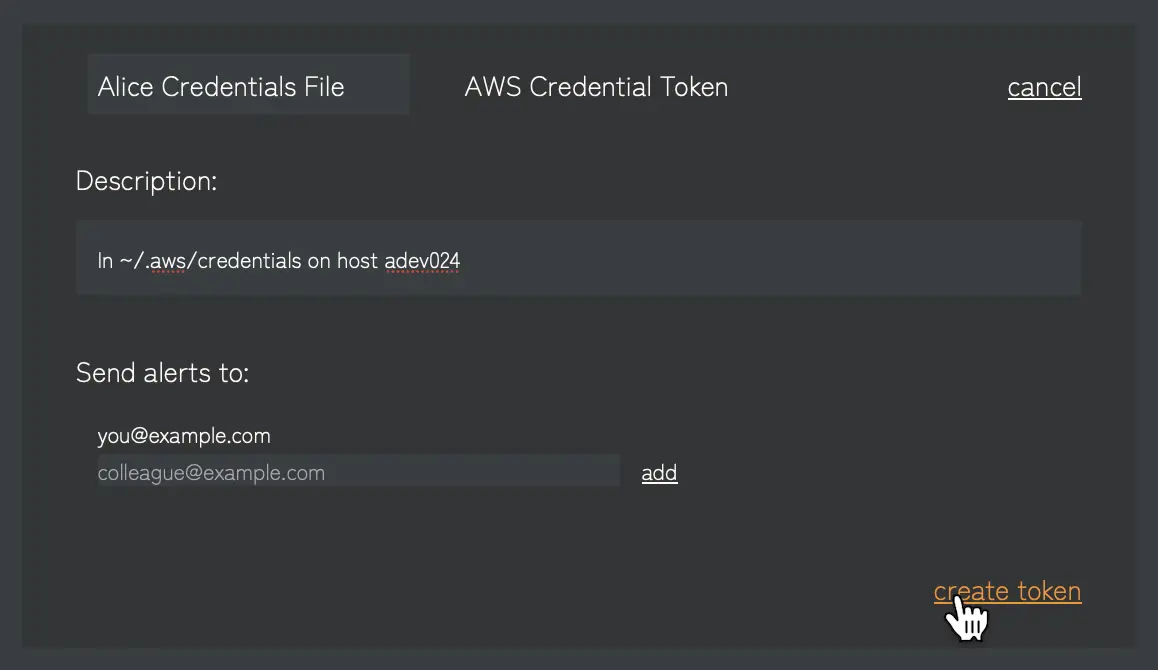
2. Enter Name and Details
Then enter a name and description for this token, and any additional email addresses that you want to send alerts to. Confirm to complete the token creation:
The name will be included in alerts sent about this token. It should tell you where the token is used, so if an alert occurs you know which device has been attacked.
The description is not included in alerts, but you can make any additional notes here to help you remember details about this token.
Your own email address is included by default in alerts. If you need to, you can change any of these details later from the tokens list.
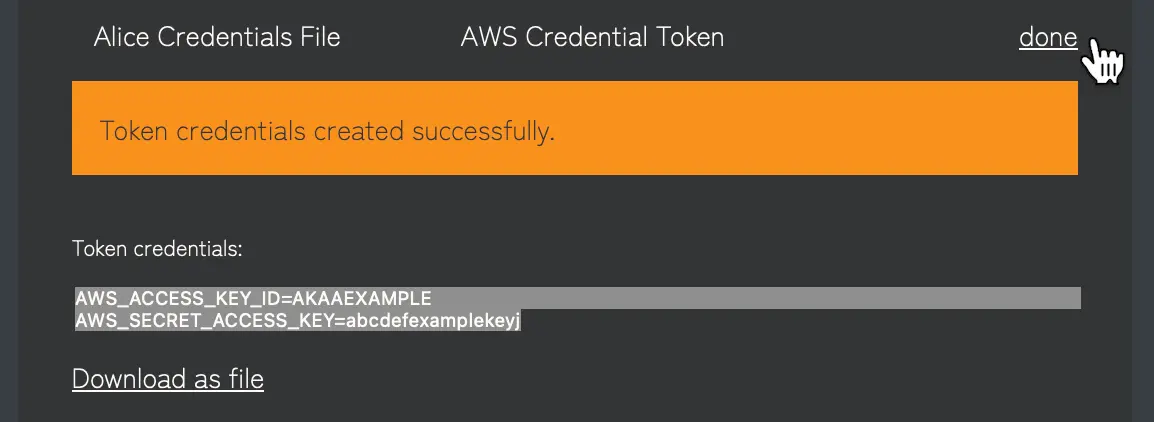
3. Copy the Token Credentials
Finally, Copy the AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY from the confirmation screen. We'll now place these canary credentials into our credentials file. If you need to, you can view these again later via "show details" > "show token credentials and setup instructions" from your token list.